AWS OpsWorks Supports t1.micro Instances
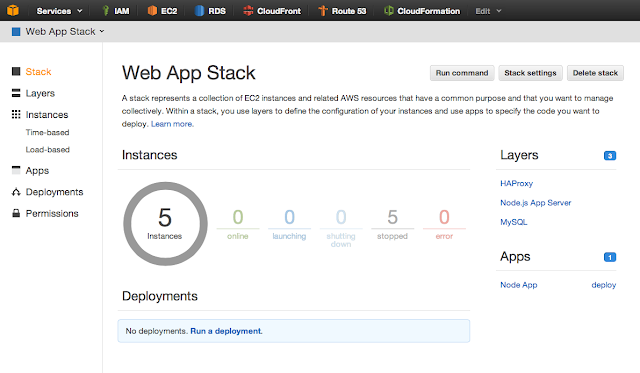
Amazon Web Services announced yesterday a long-awaited update to their OpsWorks product by including free tier and t1.micro instance types, something that has always keeping me away of trying OpsWorks, because smallest instance was always m1.small. You can provision now following instance types for your web, database, haproxy, e.t.c.: Micro t1.micro Standard 1st gen. m1.small m1.medium m1.large m1.xlarge Standard 2nd gen. m3.xlarge m3.2xlarge HighMEM m2.xlarge m2.2xlarge m2.4xlarge HighCPU c1.medium c1.xlarge HighIO hi1.4xlarge HighStorage hs1.8xlarge From operating systems only Amazon Linux or Ubuntu 12.04 LTS are supported. As with OpsWorks, you can launch web server stack behind HAProxy (Amazon reps say they will support Elastic Load Balancer very soon), and in addition to 24/7/365 servers you can prepare time-based servers and load-based spare servers, which will start/stop on demand, or "follow-the-sun" approach. AWS OpsWor